STUXNET REDUX?: ‘Are three mysterious explosions in Iran linked? – Analysis’
JERUSALEM/POST |By Jonah Jeremy Bob | July 2, 2020
A team of experts from Iran’s Atomic Energy Organization are investigating the cause of the incident.
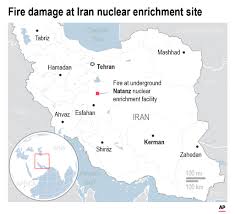
An “incident” occurred at Iran’s Natanz nuclear facility but no damage was caused and the site is operating as usual, Iran’s Atomic Energy Organization said on Thursday.
“The incident took place in a facility in an open area near Iran’s Natanz nuclear facility. There were no casualties or damages and the nuclear site is operating as usual,” Iran’s nuclear agency’s spokesman, Behrouz Kamalvandi, was quoted as saying by Iran’s Tasnim news agency.
Stuxnet is a malicious computer worm, first uncovered in 2010, thought to have been in development since at least 2005. Stuxnet targets supervisory control and data acquisition (SCADA) systems and is believed to be responsible for causing substantial damage to the nuclear program of Iran. Although neither country has openly admitted responsibility, the worm is widely understood to be a cyberweapon built jointly by the United States and Israel.[2][3][4]
Stuxnet specifically targets programmable logic controllers (PLCs), which allow the automation of electromechanical processes such as those used to control machinery and industrial processes including gas centrifuges for separating nuclear material. Exploiting four zero-day flaws,[5] Stuxnet functions by targeting machines using the Microsoft Windows operating system and networks, then seeking out Siemens Step7 software. Stuxnet reportedly compromised Iranian PLCs, collecting information on industrial systems and causing the fast-spinning centrifuges to tear themselves apart.[6] Stuxnet’s design and architecture are not domain-specific and it could be tailored as a platform for attacking modern SCADA and PLC systems (e.g., in factory assembly lines or power plants), most of which are in Europe, Japan, and the US.[7] Stuxnet reportedly ruined almost one-fifth of Iran’s nuclear centrifuges.[8] Targeting industrial control systems, the worm infected over 200,000 computers and caused 1,000 machines to physically degrade.[9]
Stuxnet has three modules: a worm that executes all routines related to the main payload of the attack; a link file that automatically executes the propagated copies of the worm; and a rootkit component responsible for hiding all malicious files and processes, to prevent detection of Stuxnet.[10] It is typically introduced to the target environment via an infected USB flash drive, thus crossing any air gap. The worm then propagates across the network, scanning for Siemens Step7 software on computers controlling a PLC. In the absence of either criterion, Stuxnet becomes dormant inside the computer. If both the conditions are fulfilled, Stuxnet introduces the infected rootkit onto the PLC and Step7 software, modifying the code and giving unexpected commands to the PLC while returning a loop of normal operation system values back to the users.[11][12]
In 2015, Kaspersky Lab noted that the Equation Group had used two of the same zero-day attacks prior to their use in Stuxnet and commented that “the similar type of usage of both exploits together in different computer worms, at around the same time, indicates that the Equation Group and the Stuxnet developers are either the same or working closely together”.[13]







